Why You Actually Need Microsoft Defender for Cloud (And What It Actually Does)

Alright, class. Take your seats.
Your infrastructure is in the cloud now. Could be Azure. Might be AWS. Probably both. Maybe GCP too, because apparently someone in your org decided multi-cloud was a good idea without asking IT first.
The problem is you've got zero visibility into whether any of it is secure.
You've got resources everywhere. VMs running God-knows-what configuration. Containers you didn't even know existed. Storage accounts full of data that shouldn't be accessible. Databases with default passwords. APIs exposed to the internet. And you're sitting there hoping nothing breaks. Hoping nothing gets hacked. Hoping your compliance auditors don't ask too many questions.
You need to stop hoping. You need Microsoft Defender for Cloud.
I'm not saying this because it's trendy. I'm saying this because if you're running cloud infrastructure without it, you're flying blind. You don't have visibility into your security posture. You're not getting alerted to threats. You're not tracking compliance. You're basically a security incident waiting to happen.
Let me explain what it is, why you need it, and how it actually helps you do your job as a SOC analyst, security engineer, or IT pro.
What Is Defender for Cloud
Microsoft calls it a CNAPP (Cloud Native Application Protection Platform). That's just fancy marketing speak for "we put multiple security tools together."
It has three main parts working together:
CSPM (Cloud Security Posture Management) is the auditor. It constantly checks your cloud infrastructure and tells you "Your storage account doesn't have encryption enabled" or "This VM allows RDP from anywhere on the internet." It's about configuration and compliance. Are your resources properly configured according to security best practices? CSPM tells you.
CWPP (Cloud Workload Protection Platform) is the guard. It watches your resources at runtime. Something tries to run malware on your VM? CWPP alerts you. Someone tries to exfiltrate data from your database? CWPP sees it. It's about detecting and stopping active threats.
DevSecOps is the developer's friend. It scans your code pipelines (GitHub, Azure DevOps, GitLab) for vulnerabilities, exposed secrets, and infrastructure-as-code misconfigurations before that code ever reaches production.
Put them together and you've got a tool that catches misconfigurations, stops threats, and stops bad code from shipping. That's Defender for Cloud. One platform covering all three angles.
Here's the Thing About Foundational CSPM vs the Paid Stuff
When you enable Defender for Cloud on an Azure subscription, you automatically get Foundational CSPM. It's free. No upsell needed.
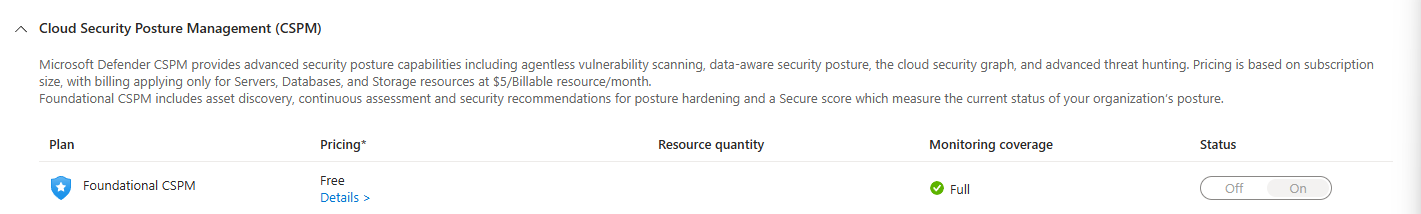
Foundational CSPM gives you:
- Asset discovery across your multicloud environment (Azure, AWS, GCP)
- Security recommendations based on the Microsoft Cloud Security Benchmark
- A Secure Score that tracks your overall security posture
- Basic compliance checking
- Connection to GitHub, Azure DevOps, GitLab for code scanning
It's not nothing. It's actually quite useful if you've never had visibility before.
But if you want the advanced stuff, you upgrade to Defender CSPM (the paid plan). Here's what you get extra:
- Attack path analysis (finding chains of misconfigurations that could lead to a breach)
- Cloud Security Explorer (custom queries to hunt for security gaps)
- Advanced threat hunting
- Data security posture management (finding sensitive data exposure)
- Governance and security governance workflows
- Entra Permissions Management (identity attack surface management)
The pricing is $5/billable resource/month, but that's only for Servers, Databases, and Storage. The posture management stuff applies across your entire environment, regardless of size.
So here's the real question: is it worth paying extra? For most organisations that actually care about their security posture, yes. The attack path analysis alone is worth it because it shows you the actual attack chains that could hurt you, not just individual misconfigurations.
What It Actually Protects (And Why You Should Care)
Defender for Cloud isn't just sitting around looking at your VMs anymore. This thing covers your entire attack surface. Let me break down what actually matters.
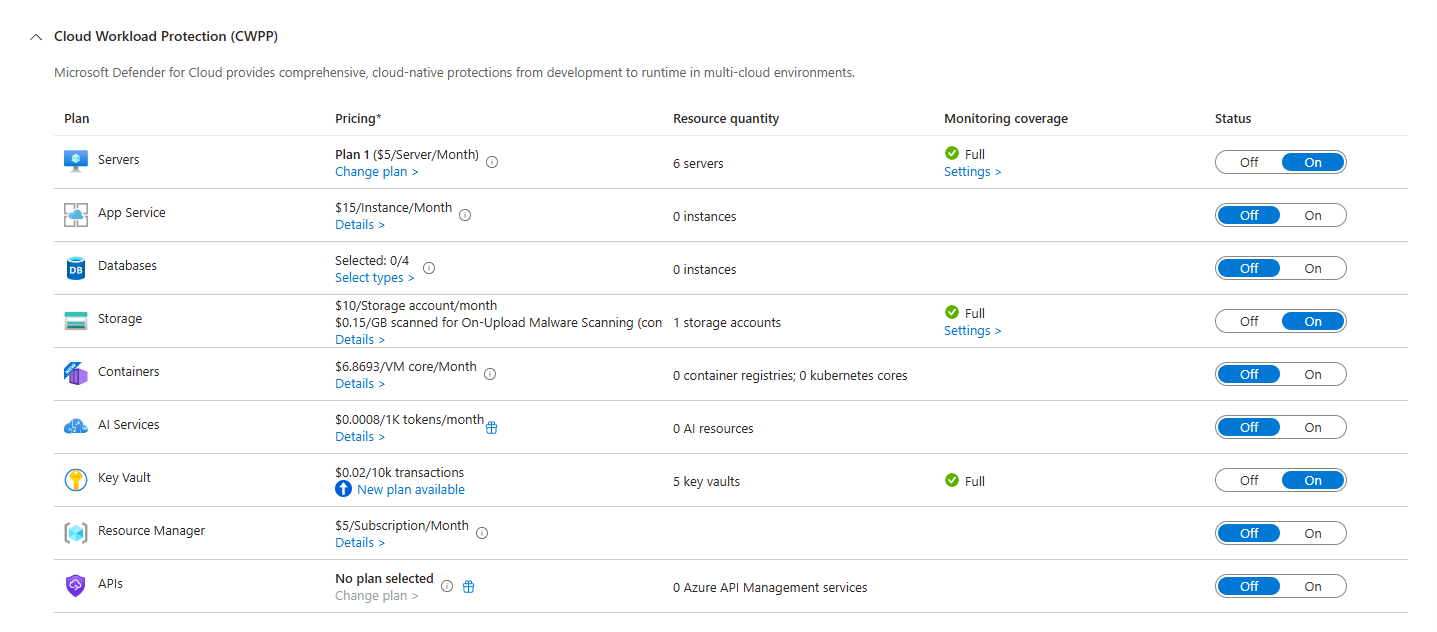
Servers (and Agentless Scanning Is a Game Changer)
You've got VMs everywhere. Azure, AWS, EC2 instances, on-premises boxes. Defender for Cloud scans all of them without installing agents.
How? It creates temporary snapshots of your VM disks, scans them in an isolated, encrypted environment, then deletes them. No performance hit. No networking requirements. No agent bloat.
Here's what agentless scanning catches that you probably don't know about: unpatched software, misconfigurations, hardcoded credentials in files, malware. It uses Microsoft Defender Vulnerability Management to find CVEs. If you've got Windows and Linux boxes running outdated versions of packages, Defender finds them. If someone accidentally committed an AWS access key to a text file on a server, Defender's secrets scanning catches it.
Real-world scenario: Your team spun up an old AMI on AWS because it was faster than building a new one. That image has unpatched vulnerabilities from 2023. Your SOC team never knew about it. Defender spots it via agentless scanning and surfaces it as a SecurityAlert. You remediate before anyone exploits it.
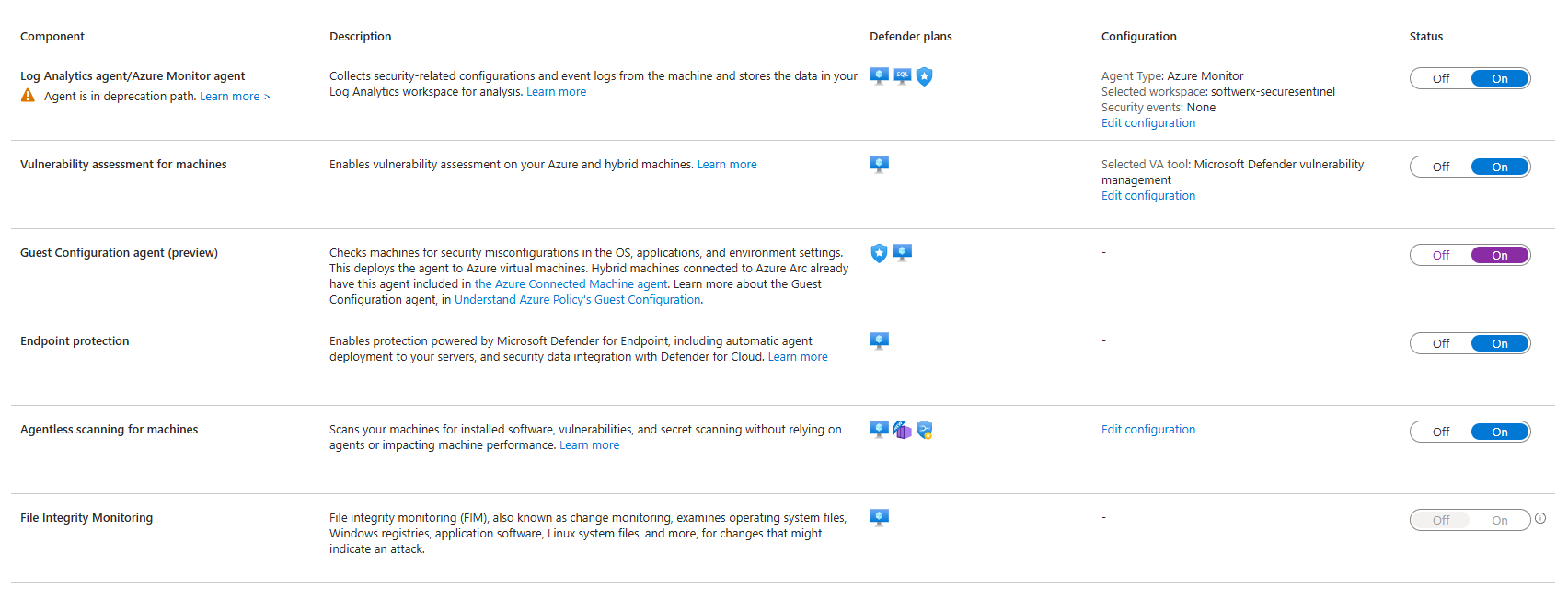
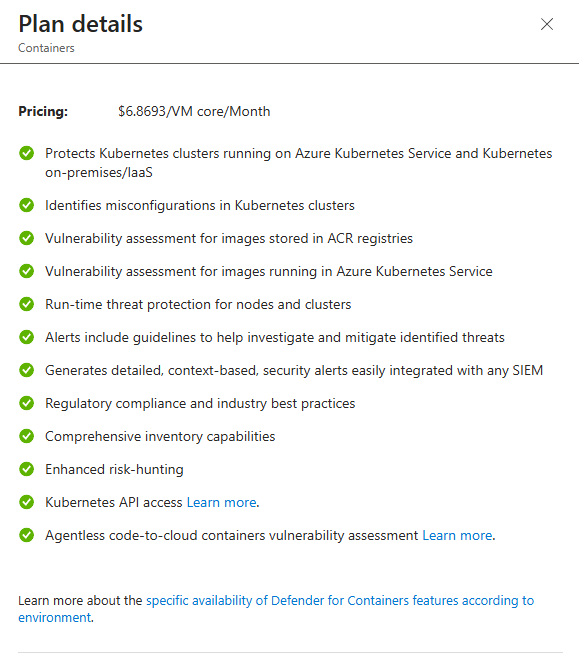
Containers (And It Actually Knows Kubernetes)
Container security is where most organisations are completely blind. Your DevOps team deploys to Kubernetes, and nobody knows if the images are vulnerable or if the cluster configuration is a disaster.
Defender for Containers scans your registry images (Azure Container Registry, AWS ECR, Google Artifact Registry, even external registries). It finds CVEs in the OS and application dependencies using Defender Vulnerability Management. That's just the static scanning.
But runtime protection is where it gets interesting. Defender deploys a DaemonSet on your Kubernetes nodes that watches for:
- Pod escape attempts
- Privilege escalation inside containers
- Suspicious process execution
- Network anomalies
- Exposed dashboards (seriously, people do this)
And it monitors the Kubernetes audit log for things like creation of high-privileged roles or suspicious API calls. If someone tries to create a ClusterAdmin role with no restrictions, Defender alerts you.
Real-world scenario: A misconfigured deployment exposes your Kubernetes dashboard to the internet. An attacker accesses it. Defender detects the unusual API calls (creating new service accounts, deploying malicious pods) and alerts your SOC before data gets exfiltrated.
Storage (On-Upload Malware Scanning Saves Your Ass)
Someone's uploading files to your Azure Storage account constantly. User uploads, third-party integrations, backup jobs, whatever. You have no idea if any of them contain malware.
Defender for Storage scans every blob as it's uploaded using Microsoft Defender Antivirus. It happens in near-real-time. If someone tries to upload a trojan, ransomware, or any known malware signature, Defender blocks it and alerts you.
This is configured at the subscription level by default. You don't have to do anything except enable the plan.
Real-world scenario: Your marketing team downloads a "free font pack" from the internet. Someone uploads it to SharePoint via the Storage account. Defender's on-upload malware scanning detects it's actually ransomware. The upload is blocked. Your incident response team gets an alert with file hashes and signatures. Crisis averted.
You can also do on-demand scanning of existing blobs if you're paranoid (you should be). Useful for incident response or compliance prep when someone says "we need to know if there's any malware in production storage."
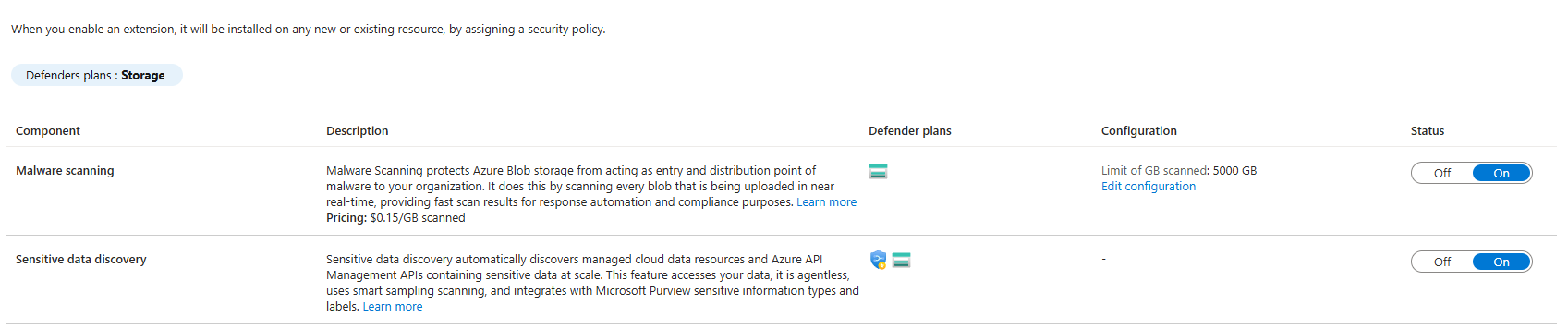
Databases (Actual Runtime Threat Detection)
You've got SQL databases, PostgreSQL, Cosmos DB, whatever. Defender monitors for suspicious activity.
What does suspicious look like? A user account that never typically connects is suddenly hammering the database with queries. Someone is exfiltrating data. Unusual batch operations. Brute force attempts on credentials.
Real-world scenario: Your compromised application server gets exploited. The attacker connects to your database with a known credential and starts running SELECT statements to dump customer data. Defender's database protection layer detects that this isn't normal activity for that user/connection pattern and alerts your SOC.
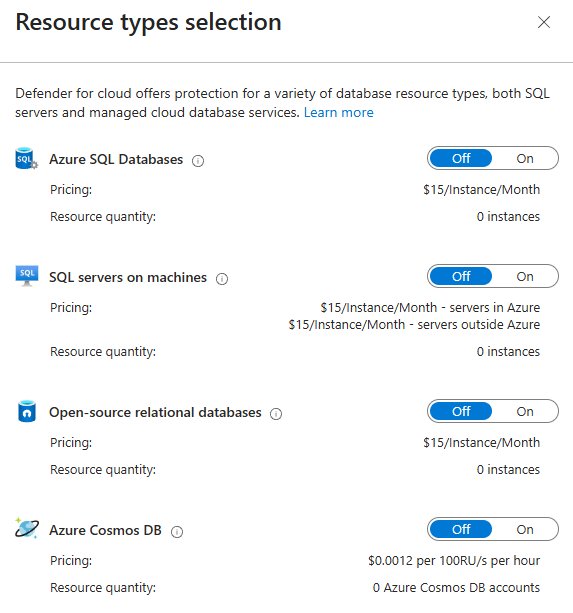
APIs (You Probably Exposed Something Without Knowing)
API Management endpoints, Azure Functions with HTTP triggers, Logic Apps that accept webhooks. All of these are potential attack surfaces.
Defender scans for misconfigured APIs: exposed internal endpoints, missing authentication, APIs that shouldn't be publicly accessible.
Real-world scenario: Your integration team deployed an API to sync customer data. They forgot to implement API key validation. Defender finds it and reports, "This endpoint is publicly accessible with no authentication." You add a managed identity requirement before it becomes a problem.
Key Vault (Because People Try to Access It Constantly)
Your Key Vault stores secrets, certificates, and encryption keys. It should never be accessed by normal operations.
Defender monitors for abnormal access patterns. Someone is trying keys they've never used before. An unusual spike in read requests. A user accessing the vault from a risky geographic location at 3 AM.
Real-world scenario: An attacker gains credentials for a low-privilege app. They discover the app's managed identity has read access to Key Vault. They attempt to enumerate secrets. Defender detects the anomalous activity and alerts you before they extract anything sensitive.
App Service (Web Applications Getting Owned Is Constant)
Your web apps run in App Service. Attacker tries SQL injection. Path traversal. Exploitation of known CVE in the framework you're using.
Defender monitors for these attack patterns. It also does vulnerability scanning on the application software running inside. If you're running Node.js 14 (end-of-life) with known vulnerabilities, Defender reports it.
Real-world scenario: Your web app is vulnerable to a CVE in an old Express.js version. An attacker finds it and tries to exploit it. Defender's runtime protection detects the malicious request pattern and alerts you. Your SOC team updates the dependency before the next attack succeeds.
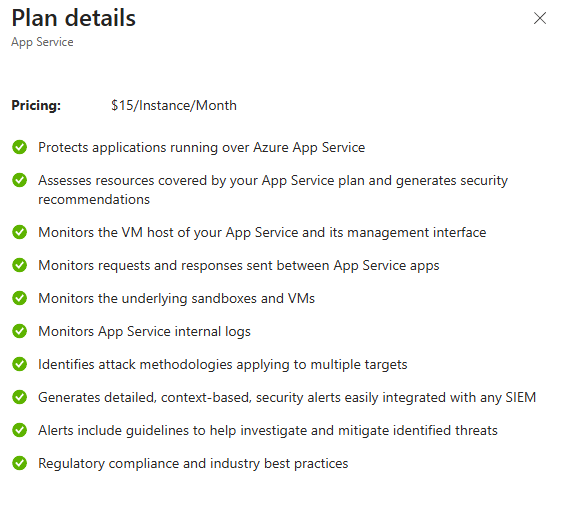
AI Services & Secrets (Newer, Actually Important)
Your team is using OpenAI, Azure OpenAI, whatever. Defender monitors for prompt injection attacks and unusual API usage patterns.
More importantly: if someone accidentally hardcodes an API key in their code, Defender's secrets scanning finds it and alerts you. This is agentless, so it works on any compute resource.
Real-world scenario: Developer commits a Databricks PAT (Personal Access Token) to a GitHub repo by accident. Defender scans the repo and finds it. Your SOC gets a SecureScores finding about exposed credentials. You revoke the token before an attacker uses it.
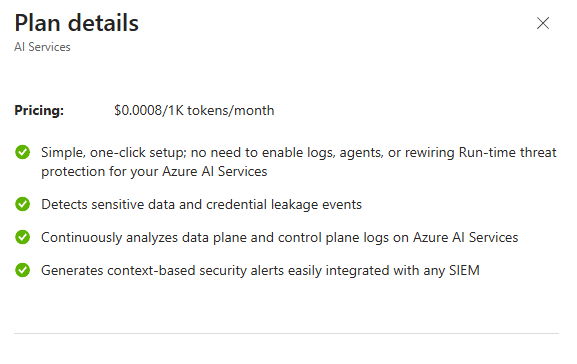
That's the actual value of Defender for Cloud. It's not just compliance checkboxes. It's real threats, real detection, real incidents that could actually hurt you.
The Multicloud Problem (And How Defender Actually Solves It)
Your infrastructure is spread across three clouds. You know it. Your CTO knows it. Everyone knows it was a terrible decision that nobody actually planned, but here we are.
Azure for some stuff. AWS for other stuff. GCP because someone in engineering thought it would be cool. Now you've got security data scattered everywhere. Azure Security Center for Azure. AWS Security Hub for AWS. Google Cloud Security Command Center for GCP. Three dashboards. Three different interfaces. Three separate compliance reports.
This is a nightmare for anyone trying to actually run security operations.
Defender for Cloud connects to all of them. You add your AWS account. You add your GCP project. Defender pulls data from all three clouds and shows you everything in one place. Not three places. One.
Real-world scenario: Your team deployed a public S3 bucket in AWS for "temporary" storage. It's been public for six months. Your GCP team misconfigured an IAM role. Your Azure environment has a storage account with default credentials. Normally you'd be checking each cloud's native security tool to find these. With Defender, you see all three problems in the same dashboard and prioritise which one to fix first.
The agentless scanning works across clouds too. Defender doesn't care if a VM is in Azure, AWS, or Google Cloud. It scans the disks, finds the vulnerabilities, and alerts you. Same interface. Same process. No "well, this cloud needs a different approach."
For your SOC team, this means you're not context-switching constantly. You're not learning three different dashboards. You're not maintaining separate incident tracking for each cloud. It's unified. One system. One workflow.
The Defender XDR Thing (Where Cloud Actually Becomes Part of Your Security)
Your Defender XDR portal is where your security team lives. Endpoint alerts. Identity threats. Office 365 phishing. All of it flows there.
Defender for Cloud integrates directly with XDR. Your cloud infrastructure findings show up in the same incident queue as your endpoint alerts.
Here's where this actually matters: correlation.
Your cloud infrastructure alert says "suspicious API activity on a managed identity." Your endpoint alert says "unusual outbound network connection from a server." Normally, you might miss that these two events are related to the same attack. In XDR, they correlate automatically. Your SOC sees the full attack chain.
Real-world scenario: An attacker compromises a server in your Azure environment. They use the managed identity to access a database and exfiltrate data. Endpoint protection detects the suspicious process. Cloud protection detects the unusual database access. XDR sees both events, correlates them, and creates a single incident with full context instead of creating two separate noise alerts your team dismisses.
The benefit isn't just correlation. It's context. You're not bouncing between Azure portal and Defender portal. Everything you need to investigate a cloud security incident is in one place. Incident timeline. Asset details. Recommendation history. All unified.
What This Means for a SOC Analyst
You're drowning in recommendations right now. Your Defender for Cloud instance fires thousands of them daily. Most are garbage. A few are actually critical.
Your job is triage. Figure out which ones matter. Communicate with the engineering team about which recommendations are legit security issues and which ones are "if we implement this, production breaks."
Defender for Cloud has a feature called Attack Path Analysis. Instead of "you have 48 security recommendations," it shows "you have 3 attack paths that could actually lead to a breach."
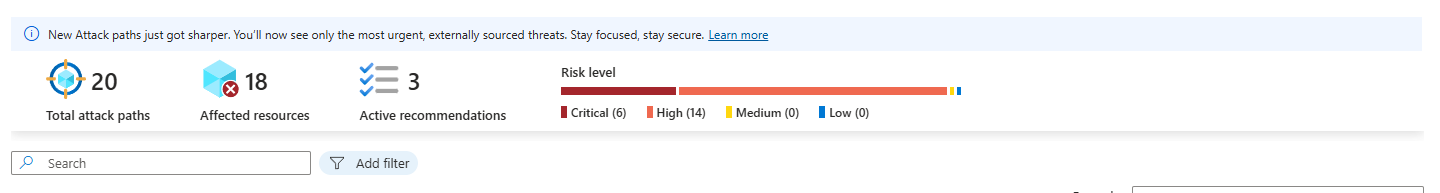
An attack path is a chain of misconfigurations that an attacker could exploit. Example: "VM has public IP + default network security group allows RDP from anywhere + OS is unpatched + admin account has weak password = attacker can compromise this VM and pivot to your database."
That's what matters. Not "update this one thing." But "fix these three things together or you've got a real problem."
Real-world scenario: You're overwhelmed. 500 open recommendations. Engineering team tells you they can't fix everything tomorrow. You run Attack Path Analysis. It shows 12 critical paths. You tell engineering "these 12 chains of misconfiguration need to be fixed. The other 488 recommendations can wait." Now you've got something engineers can actually action.
This changes everything for SOC operations. You're not dealing with noise. You're dealing with actual risk.
For Engineering Teams (Your Feedback Loop)
You deploy something to Azure. Five seconds later, Defender is telling you it's misconfigured.
Forgotten security group rule? Defender finds it. Hardcoded credentials in a config file? Detected. Unpatched OS? Caught. Storage account with public access? Alert.
The old way: deploy, wait six months for an audit, discover you did everything wrong, then have to refactor. Defender flips this. Deploy, get feedback immediately, and fix it before it matters.
This is continuous improvement. You're not waiting for compliance reviews. You're getting security feedback in real-time as you build infrastructure. That's actually useful for engineering teams.
Compliance Reporting (Finally Something That Doesn't Suck)
Your compliance team needs to track ISO 27001. NIST. PCI-DSS. GDPR. Whoever your auditors are this year.
Normally, this means spreadsheets. Manual checks. "Are your storage accounts encrypted?" Someone has to click through every storage account and verify. Multiply that by hundreds of resources across three clouds.
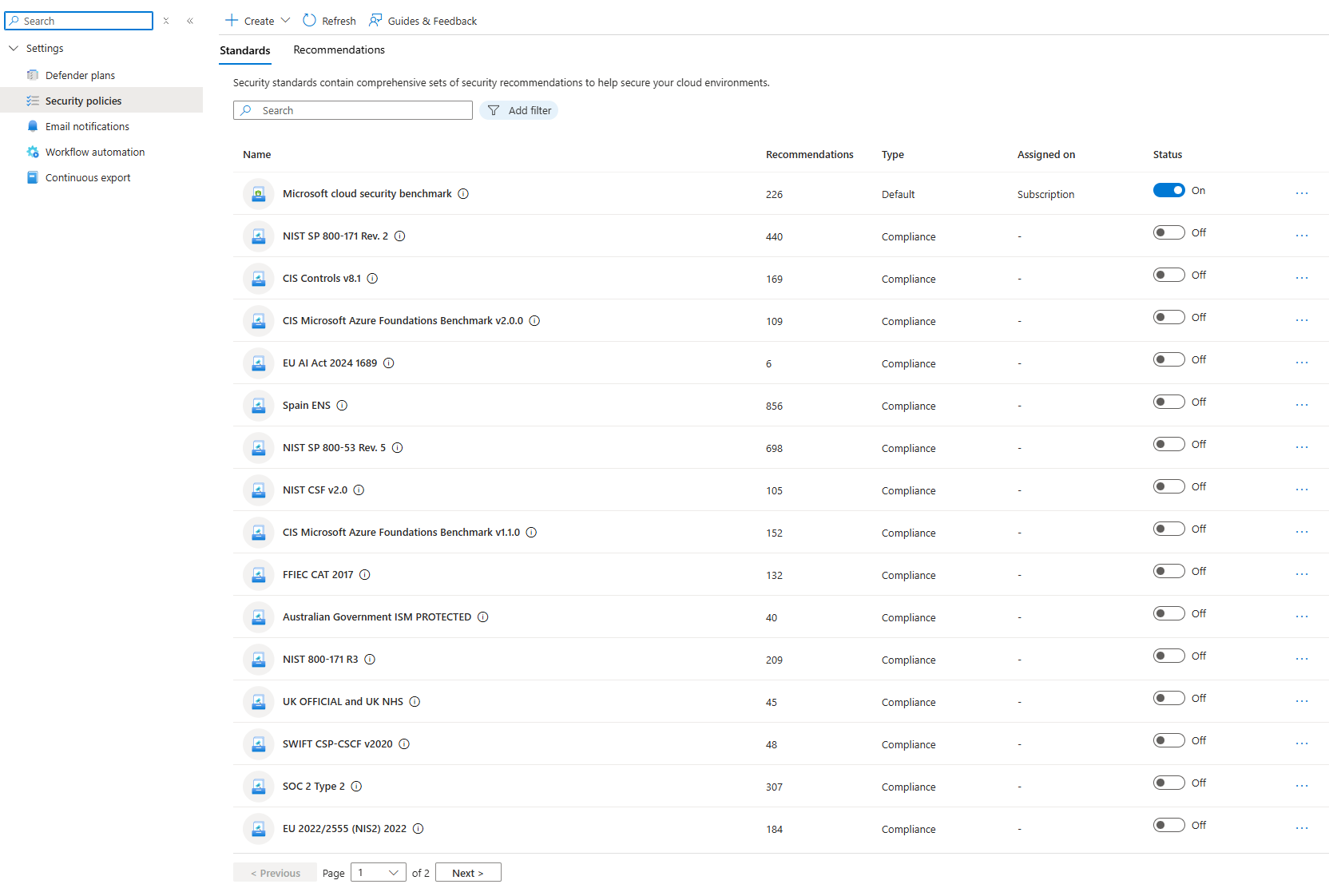
Defender has 450+ compliance frameworks built in. It runs all the checks automatically. It tells you which resources are compliant and which aren't. It tracks your compliance score over time. It generates reports.
Real-world scenario: Your audit is next month. Your compliance team would normally spend weeks manually verifying everything. With Defender, they run a report. Defender tells them exactly which resources are non-compliant and why. Remediation work gets prioritised. The report is generated. Auditor signs off.
This saves your compliance team weeks of manual work and reduces the chance of missing something that gets flagged in the audit.
So, Why Actually Enable This?
Because flying blind is amateur hour.
You can either know your cloud security posture or you can guess. One of those gets you breached. The other gets you a promotion.
Start with Foundational CSPM. It's free. It's not the full experience, but it gives you basic visibility. Try it. See what it finds.
If your organisation actually cares about security (not just compliance theatre), upgrade to Defender CSPM. $5 per billable resource per month. Connect AWS. Connect GCP. Enable the workload protection plans that matter to your infrastructure.
Then use the data. Don't just collect it. Look at the attack paths. Investigate the alerts. Work with engineering to fix things. Track your Secure Score, improving month over month.
That's the difference between having a security tool and actually using it
Class dismissed.
